•
Cryptography
–
Science of changing plain text into cipher text
by substituting or transposing characters
–
Uses algorithms (mathematical formulas) and keys
to create cipher text
•
Earliest cryptography relied on human effort to
create, break codes; today computers are used
Earliest Methods of Cryptography
•
Substitution ciphers
•
Maps each letter to another letter
•
Prone to frequency analysis
•
Vigenere cipher
–
Polyalphabetic substitution
•
Substitutes cipher letters according to keyword
•
Assigns number values to letters (a=0)
•
Adds value of each letter in keyword to letter
values in plain text in order
–
If you know length of key, can break cipher text
into multiple simple substitution ciphers
Encryption with Vigenere Cipher
Breaking Vigenere Cipher Text Into
Simple Substitution Ciphers
Simple Substitution Ciphers
Earliest Methods of Cryptography
•
One-time pad
–
Pad of paper with random selection of numbers
(two copies)
–
To encrypt, first letter of plain text shifted
by first number on pad, second letter by second pad number, etc.
•
Historic ciphers
–
Enigma: WWII German machine creating complex
substitutions
–
Purple: WWII Japanese machine modeled after
Enigma
Cryptographic Primitives
•
Primitives: Four main areas of cryptography
–
Random number generation
–
Symmetric encryption
–
Asymmetric encryption
–
Hash functions
•
Goals of cryptography: Confidentiality,
integrity, authentication (CIA)
Random Number Generation
•
Computer-generated random numbers are
pseudorandom
–
Computers cannot create fully random numbers
•
Goal is unpredictability
•
Depth concern: Algorithms cycle, repeat
•
Two cryptographically secure pseudorandom number
generators
–
Blum-Blum-Shub pseudorandom number generator
RSA pseudorandom number generator
Symmetric Encryption
•
Single-key encryption
–
Same key used to encrypt, decrypt
•
Used for confidentiality
•
May provide integrity depending on mode used
•
Analogy is lockbox
–
Single key required
–
Key is set of random bits
•
Encryption strength depends on algorithm or
cipher used
–
Computationally secure: Time needed to
compute all combinations is so large, can’t be done in reasonable amount of
time
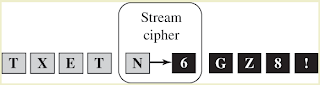
Stream Ciphers
•
Type of symmetric encryption
•
Stream of data: Each byte processed with
preceding bytes; order is important
•
Stream Cipher
–
Uses single key to encrypt message or stream of
data, e.g. one-time pad
–
Does not require padding
–
Provides integrity: If first bytes changed,
errors propagated through message
Stream Cipher
Block Ciphers
•
Type of symmetric encryption
•
Blocks of message processed independently
•
Must safeguard against:
–
Identification of repeated blocks
–
Changing of block order
Sharing Keys
•
Keys: Must be known by both parties before
algorithm can be used
•
Sharing options
–
“Pre-shared secret”
–
Trusted third party
–
Key agreement protocol
•
E.g. Diffie-Hellman key exchange
•
Prone to man-in-middle attack
Man-in-the-Middle Attack
•
Requires use of two keys
–
Private key known only by owner
–
Public key available to users
•
Public key used to encrypt data that only
recipient with private key can read
•
Because asymmetric encryption very slow, often
used just to encrypt symmetric encryption key
•
Digital signature: Encrypts small attachment to message with
private key to verify ownership
Digital Signature of Hash
Hash Functions
•
Take messages and compute smaller, fixed-size
message (digest, or hash)
•
Provide better performance
•
Provide integrity: Message always hashes to same
digest
•
Used in authentication blocks
•
Used to create pseudorandom data
•
Useful for storing passwords: However, passwords
should be salted with pseudorandom values
•
Keyed hash functions are designed to require
keys
Salting
Internet Options Dialog Box
sampai sini ja sempat explore !
Penah jugak jumpa benda neh ? kalau yang guna server yang ada security msti ada. try cari .
HAHA . crytography neh sangat best !
sebarang penambahan buleh ja .silakannnn ..